Configuring the Windows Launcher
Introduction
To learn about the Launcher’s role in Login Enterprise, what it does, how it works, and more, see Launchers Overview and Best Practices.
For details on where the Launchers architecturally reside in the Login Enterprise setup, see the System Architecture and Components.
Downloading and Installing the Windows Launcher
Log in to your Login Enterprise with the Launcher intended to be the host.
In the Sidebar menu, navigate to Configuration > Launchers.
In Launchers, select Downloads from the tab bar menu and download the file.
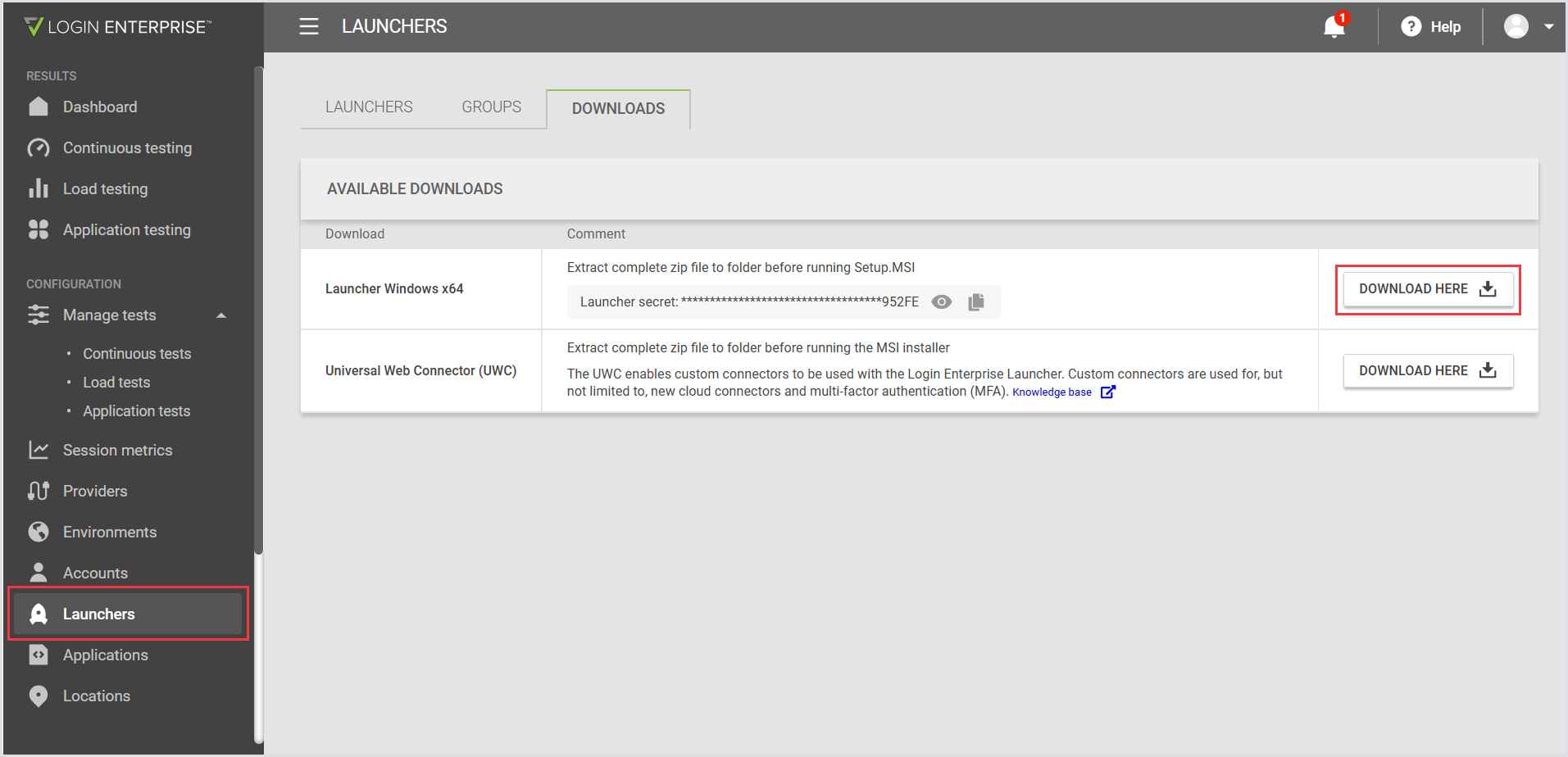
Alternatively, the Launcher can be downloaded from the sidebar menu under Other > Downloads.
Once downloaded, extract the Launcher zip file.
Start the Launcher installation by running the Setup.msi file, following the prompts.
The Launcher will launch by default at the end of the installation.
Installation Directory
You can save the extracted Launcher installation directory on a shared network location. This way, you can access it quickly without downloading and extracting it each time you set up a new Launcher.
Silent Installation
You can use command-line functions to simplify the deployment and update processes for the Launcher installation.
To run the MSI file silently, use the following parameters. Be sure to replace <URL> and <secret> with your specific values:
msiexec /I "<full path to Setup.msi>"/qb! serverurl=<FQDN of appliance> secret=<secret>For example:
msiexec /I "\\fileserver\share\Setup.msi"/qb! serverurl=https://loginvsi.demo.com secret=E0733F0B555035C7E377CA8797530855770141C1Copy the secret from the Downloads > Launcher secret:
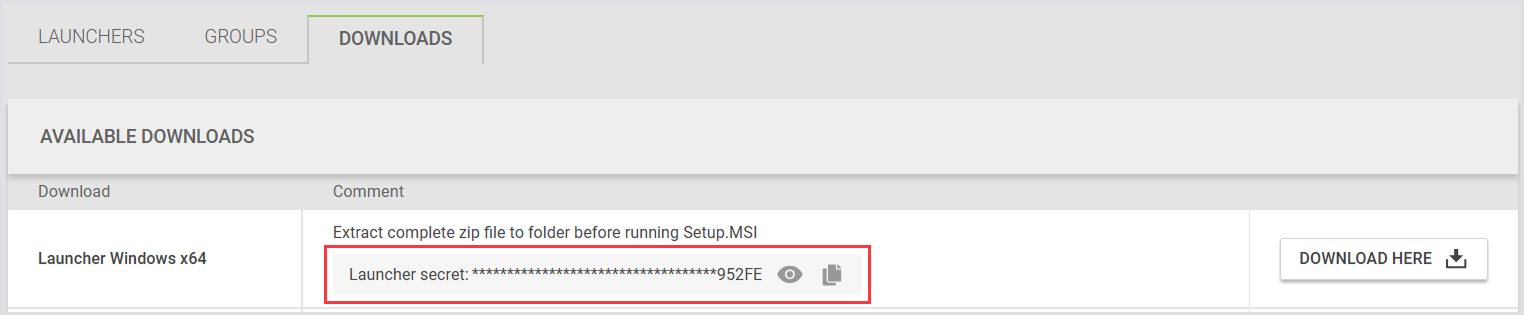
Using silent installation for the Launchers allows administrators to streamline the deployment process, reduce potential human error, and ensure consistent configurations across all systems.
Silent installation supports automated, programmatic deployment.
Running, Operating, and Starting the Windows Launcher
Ensuring Proper Connection
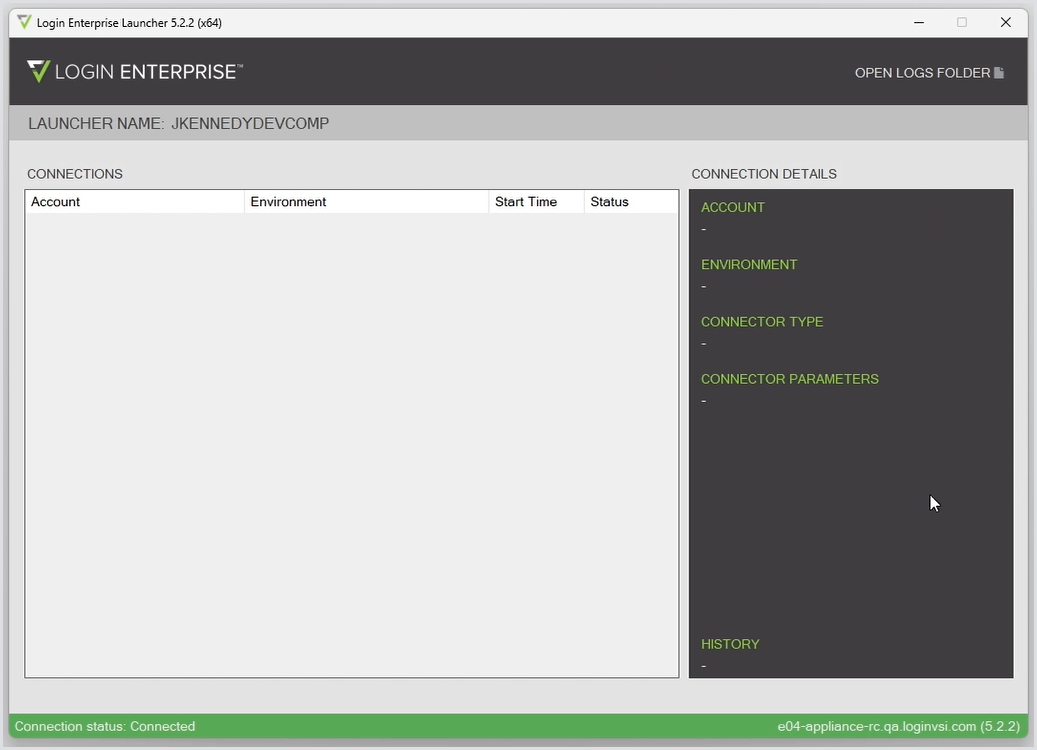
When you run the Launcher, check the bottom toolbar of the UI. It will indicate if the Launcher is successfully connected to the appliance from which the installer was originally downloaded.
Accessing the Windows Launcher
Enabling Remote Connectivity to the Launcher
If you are using a physical Launcher machine, we recommend enabling remote connectivity. Options include Remote Desktop Protocol (RDP), TeamViewer, Virtual Network Computing (VNC), or other remote access applications. Remote access simplifies troubleshooting when necessary.
Enabling Verbose Logging for the Launcher
To enable more detailed logging for the Launcher, modify the appsettings.json file located in the installation directory of the Launcher. By default, this path is C:\Program Files\Login VSI\Login PI 3 Launcher\appsettings.json
In the appsettings.json file, change the value of "Default" from Information to Verbose.
Maintenance and Updates
For the optimal performance of the Launcher, follow these best practices
Restart the Launcher periodically.
Have the Launcher run automatically upon startup.
Update the Launcher with each Login Enterprise release.
To ensure compatibility with each Login Enterprise release, you must manually install the new version of the Launcher. Currently, there is no automatic update mechanism available. However, you can create a script to perform a silent installation of the new Launcher over the old version using a Launcher installer stored centrally, such as on a network share.
After installing a new version of the Virtual Appliance, navigate to Launchers in the Login Enterprise sidebar menu. Download the updated version and install it over the existing Launcher.
The installation of the new version will overwrite the previous version without requiring any additional steps. For more detailed information, see Lifecycle of the Launcher and Launcher Best Practices.
Starting the Windows Launcher
Manually Starting the Launcher
By default, the installation creates a desktop shortcut for the launcher. To manually run the Launcher, double-click the shortcut on your desktop. The shortcut points to the installation path: "C:\Program Files\Login VSI\Login Enterprise Launcher\LoginEnterprise.Launcher.UI.exe".
Automatically Starting the Launcher
You can configure the Launcher to start automatically when Windows starts. There are several methods to achieve this:
Option 1: Using the Startup Folder
Copy the Launcher shortcut:
After installation, the shortcut is located on the desktop.
Open the Startup folder:
Press
Win + Rto open the Run dialog.Type
shell:startup(for the current user) orshell:common startup(for all users) and press Enter.
Paste the Shortcut:
Paste the copied launcher shortcut into the Startup folder. This ensures the launcher starts automatically when a user logs in.
Option 2: Using a Workspace Management Tool
For domain users or domain-attached launchers, consider using workspace management tools such as VMware UEM or Ivanti:
Integrate with Workspace Management tool:
Attach a login action to the launcher device or user.
Configure the tool to execute the Launcher executable found in the installation directory (by default located at "C:\Program Files\Login VSI\Login Enterprise Launcher\LoginEnterprise.Launcher.UI.exe").
Option 3: Configuring Automatic Logon in Windows
To streamline operations and reduce manual intervention, you can enable automatic login after scheduled restarts by configuring specific registry keys:
Registry Location:
HKLM:\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
Registry Keys:
AutoAdminLogon
Type: REG_SZ
Value: 1 (enabled) or 0 (disabled)
Enables automatic administrator logon functionality.
DefaultDomainName
Type: REG_SZ
Value: Your domain name (if applicable)
Specifies the domain name for the user.
DefaultPassword
Type: REG_SZ
Value: The user's password
Sets the password for auto-login.
DefaultUserName
Type: REG_SZ
Value: Username
Specifies the username for auto-login.
AutoLogonCount
Type: REG_SZ
Value: 1 (once), 2 (twice), etc.
Configures the number of times the machine stores the configuration.
Ensure the following registry keys are disabled for the above settings to work:
Registry Location:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
DontDisplayLastUsername
Type: REG_SZ
Value: 0 (disabled) or 1 (enabled)
Controls the display of the username on the logon screen.
Registry Location:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
DisableAutomaticRestartSignOn
Type: REG_DWORD
Value: 0 (disabled) or 1 (enabled)
Enables or disables automatic sign-on for users.
Using Sysinternals "Autologon" tool
The Sysinternals section of Microsoft support offers a tool called "Autologon" which simplifies the process of automating the autologon feature on a machine. To utilize the tool, follow these steps:
Visit the Autologon v.3.10 provided by Microsoft support to access detailed instructions on downloading and using the "Autologon" tool.
Download the "Autologon" tool from the provided link.
Follow the instructions provided in the guide to configure autologon for your machine.
Option 4: Creating an Executable for Automatic Logon
For a successful and secure implementation, you can create an executable using a tool like AutoIT. This executable will be executed before the automatic reboot of a machine and will contain the implementation of the registry keys described earlier. Ensure that the "AutoLogonCount" registry value is set to 1.
The rationale behind using an executable is twofold:
The executable compiles and encrypts the content, ensuring that all values, including passwords, are securely stored. For example, PowerShell scripts store values as plain text, which can pose a security risk.
By default, the "DefaultPassword" value stores the password as plain text in the registry. This means that if a person with malicious intent gains access to the device, they can see the password stored in the registry. Using an executable in conjunction with the "AutoLogonCount" registry key ensures that after the reboot, the registry entries are cleared, eliminating any security issues.
Windows Launcher User Interface
When the Launcher loads, pay attention to the Login Enterprise Launcher menu window:
Menu option | Definition |
Top bar | Shows the Launcher version |
Launcher name | The launcher name defaults to the machine name where the launcher software is installed. If a specific name is required for a launcher, it should match the name of the machine. |
Connections pane | Shows active and historical Test session connections and status |
Right-side menu | Shows connection information for selected connections |
Open logs folder | Shows deeper troubleshooting information, if needed |
Bottom Launcher connection status banner | If the banner is green, the connection to the Login Enterprise virtual appliance is successful. The appliance hostname and the appliance version are at the right of the connection status banner. |
Troubleshooting and Best Practices
Certificate Update
If a new certificate is uploaded to the appliance, we recommend reinstalling the launcher software.
Connection Status
Pay attention to the Launcher's UI bottom toolbar. If there's a connection error, the toolbar won't be green. Additionally, check the Launcher page in the Login Enterprise web interface for the Launcher's hostname; if it doesn't exist, a connection error may be occurring. Sometimes, the log files in the %appdata% path for the logged-in Launcher user can provide helpful information, so remember to check them as well. For instructions on how to do this, see the procedure below. Launcher debug level logging can be enabled by adding a Launcher to a Test. For more information, see Adding a Launcher to a Test.
Connection Failure Overview
When running the Login Enterprise Launcher, whether for the first time or after extended use, you may encounter issues where a session fails to log on. This is typically indicated by a "Connection failed" message in the Login Enterprise Launcher menu > Connection details.
Diagnosing Connection Failure
Connection issues can vary based on the connector type used. To diagnose the issue, you need to examine the log files of the Launcher.
Locate the log files in the %tmp%\LoginEnterprise\Launcher\Logs folder on your machine.
These logs contain detailed activity records of the Launcher. Each file presents a comprehensive list of events.
Identify the timestamp of the failed session from the Launcher overview.
Open the corresponding log file and search for the timestamp to pinpoint the events during that session.
Look for the event type "ConnectionFailed," which is automatically recorded whenever a connection attempt fails.
Trace back through the log entries to determine the cause of the failure. In the example below, the issue was related to the unavailability of a resource called "Test".
You can also send the log files along with your inquiry to our support team at support@loginvsi.com.
Versioning Notice
The Launcher app won't connect to a virtual appliance that's one version ahead of it. For example, if the Launcher app is version 5.9.99 and the virtual appliance (VA) is version 6.0.0, they will still communicate, but the Launcher won't attempt to launch Target connections.
Launcher Process Issues
In some environments, the Launcher process may freeze or become unresponsive. This typically indicates an environmental issue and may occur inconsistently. To address this in the short term while investigating the root cause, you can use our API to check whether the Launcher is active from the Virtual Appliance's perspective.
The sample code can be scheduled to run as a task that validates whether the Launcher is running and can restart it if necessary. This script is designed to initiate the Launcher when it is not running.
You can download the script from here.
Setup instructions
API key and FQDN: Obtain a read-only or higher API key and the Fully Qualified Domain Name (FQDN) of the Virtual Appliance. This FQDN is the same as the address used to access the Virtual Appliance interface. You can generate a new API key in the External notifications section in the Login Enterprise sidebar menu.
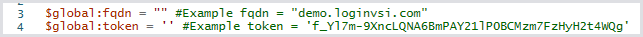
Edit the script:
Place the FQDN within the quotes on line 3.
Insert the generated API token in the single quotes on line 4. The single quotes on line 4 are intentional to accommodate special characters in the API token.
Best Practices
Recommended deployment: two Launchers - For optimal performance, deploy two Launchers per environment:
One Launcher within the data center: used to gauge connectivity and establish baseline measurements.
One Launcher outside the data center: used to assess real-world variations from the baseline.
This comparison helps identify potential performance degradation from either the connection to the data center or the data center itself. It also assesses environment accessibility from both internal and external perspectives.
Configuring the Launcher (Windows) - To ensure a successful implementation of the Login Enterprise Launcher on Windows, perform several configurations on the machine:
Automatic reboots for the Launcher
Scheduled reboots for stability
To mitigate caching issues and other potential instabilities arising from prolonged uptime, schedule regular reboots for the Launcher machine. Set up a scheduled task within Windows to automatically reboot the machine on a daily or weekly basis.
For detailed instructions on setting up a scheduled task in Windows, see Windows Server – Schedule a Reboot.
Power, Lock Screen, and Screensaver settings - To ensure the continuous operation of the Launcher, it's essential to prevent interruptions caused by power-saving modes, lock screens, and screensavers. Follow these steps to configure the necessary settings:
Power Settings:
Set the screen setting "On battery power, Turn off after" to Never.
Set the screen setting "When Plugged, Turn off after" to Never.
Set the power setting "On battery power, PC goes to sleep after" to Never.
Set the power setting "Sleep when plugged in, PC goes to sleep after" to Never.
Set the "Lid close action" for both "On battery" and "Plugged In" scenarios to Do Nothing.
Set the "Power button action" for both "On battery" and "Plugged In" scenarios to Do Nothing.
Set the "Sleep button action" for both "On battery" and "Plugged In" scenarios to Do Nothing.
Other Settings:
Disable the screensaver on the machine.
Disable the lock screen on the machine.
Deployment and Compatibility
Physical Launcher Setup
When configuring the Launcher as a physical device, prioritize security and minimize the risk of unauthorized access by following these best practices:
Secure placement - Place the Launcher machine in a secure location, such as a locked storage room or server room. Limit access to the room as much as possible to minimize the risk of unauthorized entry.
Kensington lock - Ensure that the device supports the use of a Kensington lock to prevent easy removal from the secure location.
Device selection for security - To mitigate potential security risks, use a physical device without an attached screen. Avoid using laptops and instead opt for devices such as Intel NUCs, desktop machines, Windows Thin clients, IGEL Thin clients, or similar alternatives. If a laptop is used, ensure that the lid is closed at all times.
Stable connection - To maintain a stable connection, connect the Launcher to the internet using a wired LAN cable. Use wireless connections only when necessary.
IT Environment Launcher Implementation
Extend security considerations for the Launcher beyond the physical realm by following these recommendations:
Avoid adding a Launcher device to the domain - For management or remote connectivity, refrain from adding the Launcher machine to the Domain unless necessary. This reduces the risk of unauthorized access to the domain if the device is compromised.
Updates and upgrades - Ensure that the Launcher device is consistently updated with the latest security patches recommended by the software supplier.
Add Launcher to automatic software distribution method - Enhance manageability and streamline software upgrades for the Login Enterprise by adding the Launcher machine to your preferred software distribution setup, such as SCCM or similar tools. This enables easy distribution of new Launcher software updates as soon as they are released.
Virus scanner configuration - Configure and maintain a virus scanner on the Launcher machine at all times. Ensure the virus scanner is updated regularly to provide optimal protection against threats.
Windows Launcher Requirements
The Login Enterprise Launcher machine initiates sessions to the target environment. It must be a separate virtual or physical machine.
A Launcher has a maximum capacity of 30 concurrent sessions. If you use custom connectors, the maximum capacity may vary. Additionally, the launcher needs to run in an interactive session to ensure that the appropriate client software can be executed, and graphic content from the protocol is displayed.
For more information on connectors and connection options, see Configuring Connectors and Connections.
Operating Systems
To run the Launcher software, Login Enterprise is compatible with the following Launcher operating systems:
OS Vendor | Versions |
Windows | |
IGEL | |
Debian | |
Ubuntu | |
Fedora |
Software Requirements
To ensure the Launcher is working accurately, the Launcher needs to have certain software available. All Launchers need a vendor-specific connector to connect to the Test platform.
Windows
Microsoft .NET Framework 4.8 or higher
Citrix Receiver / Citrix Workspace
VMware Horizon Client
Linux
Curl
XDOTool
OpenSSL
Free RDP
Citrix Receiver / Citrix Workspace
VMware Horizon Client
Antivirus and App Blocker Exclusions
To ensure optimal performance and prevent conflicts, certain files and processes need to be excluded from antivirus scans and app blocking. Add the following exclusions to your antivirus or app blocker to ensure the Login Enterprise runs correctly.
Launcher Machine
Enterprise Launcher software
C:\Program Files\Login VSI\Login Enterprise Launcher\LoginEnterprise.Launcher.UI.exe
Universal Web Connector
C:\Program Files\Login VSI\Universal Web Connector\UniversalWebConnector.exe
Target VM
Login Executable
LoginPI.Logon.exe
The path will depend on the policy/configuration of the environment
Enterprise engine
%TEMP%\LoginPI\Engine\LoginPI.Engine.exe
Login Enterprise EUX Applications
%TEMP%\LoginEnterprise\EuxApp
AppSpeed.exe
CompressionSpeed.exe
CpuSpeed.exe
DiskSpeed.exe
eux2023.zip
Login Enterprise EUX work files
My Documents\eux2023
%LOCALAPPDATA%\eux2023
Hardware Requirements
For optimal functionality of Launchers, you need to configure the minimum hardware requirements. The following specifications represent the minimum requirements applicable to machines running Windows, Linux, and Azure environments:
Configuration | CPU | Memory | Disk |
Minimum | 2(v)CPU | 4GB RAM | 1GB free space |
.png)